Identity and access management (commonly known as “IAM”) is a difficult task for any secure network. Distributing access credentials, assigning identities and roles, scoping permissions, etc. become exponentially more complex with the growing number of dispersed, independent edge assets:
To address these concerns, Xaptum provides secure hardware-based credential management coupled with in-field identity provisioning:
Such hardware-secured credential and in-field identity management is available in addition to a traditional PKI-style option. For machines in data centers or clouds or just individual PCs, individual management of keys and certificates is appropriate, so Xaptum supports that flow as well and can integrate with a customer’s existing PKI setup.
TPM is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys. This microprocessor contains unique, secure credentials and its security functions (illustrated below) primarily enable the authentication of what would otherwise be an untrusted device.
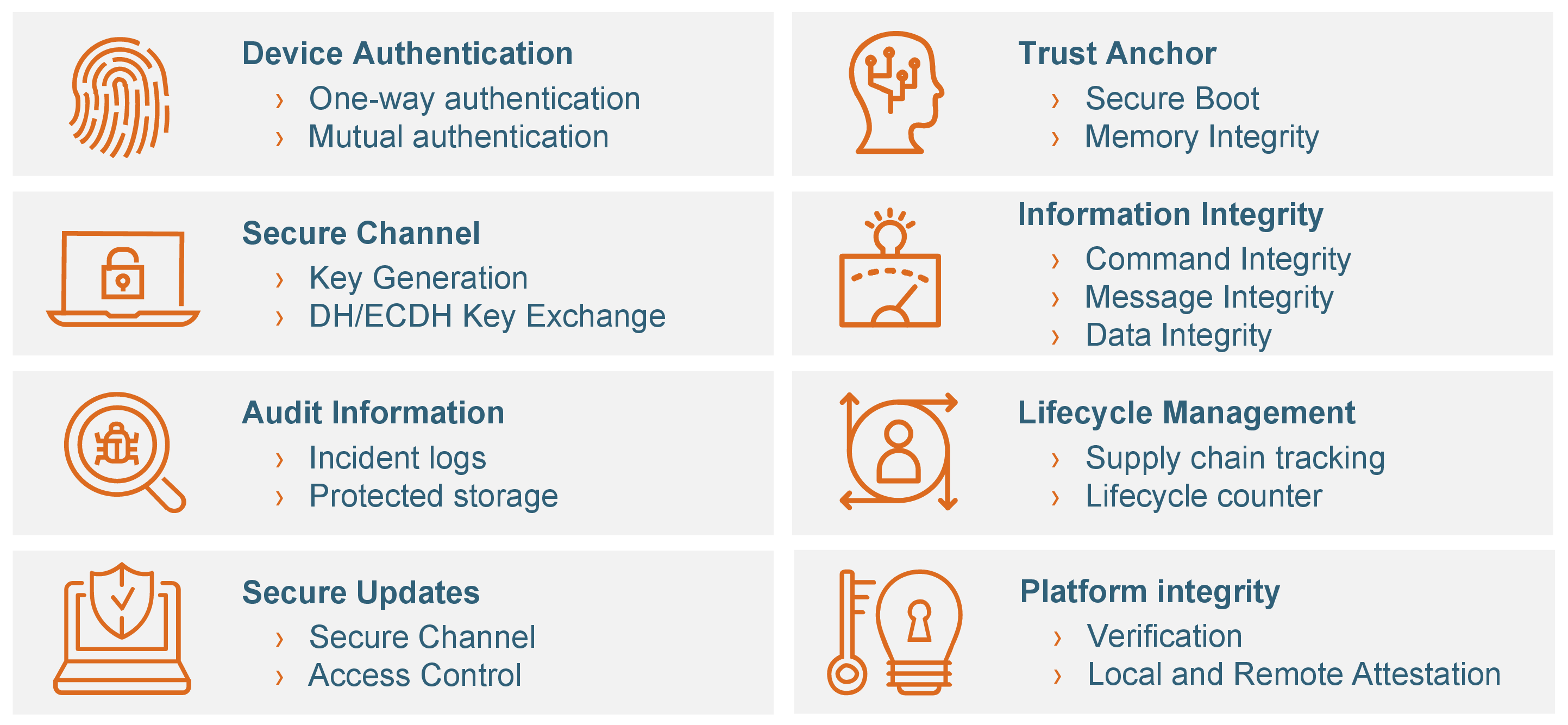
TPM Security Functions
Xaptum recommends the TPM approach for devices to connect to the ENF. The edge device may be designed and manufactured with an onboard TPM chip or it may make use of an expansion card such as an access card or router card that contains a TPM chip.
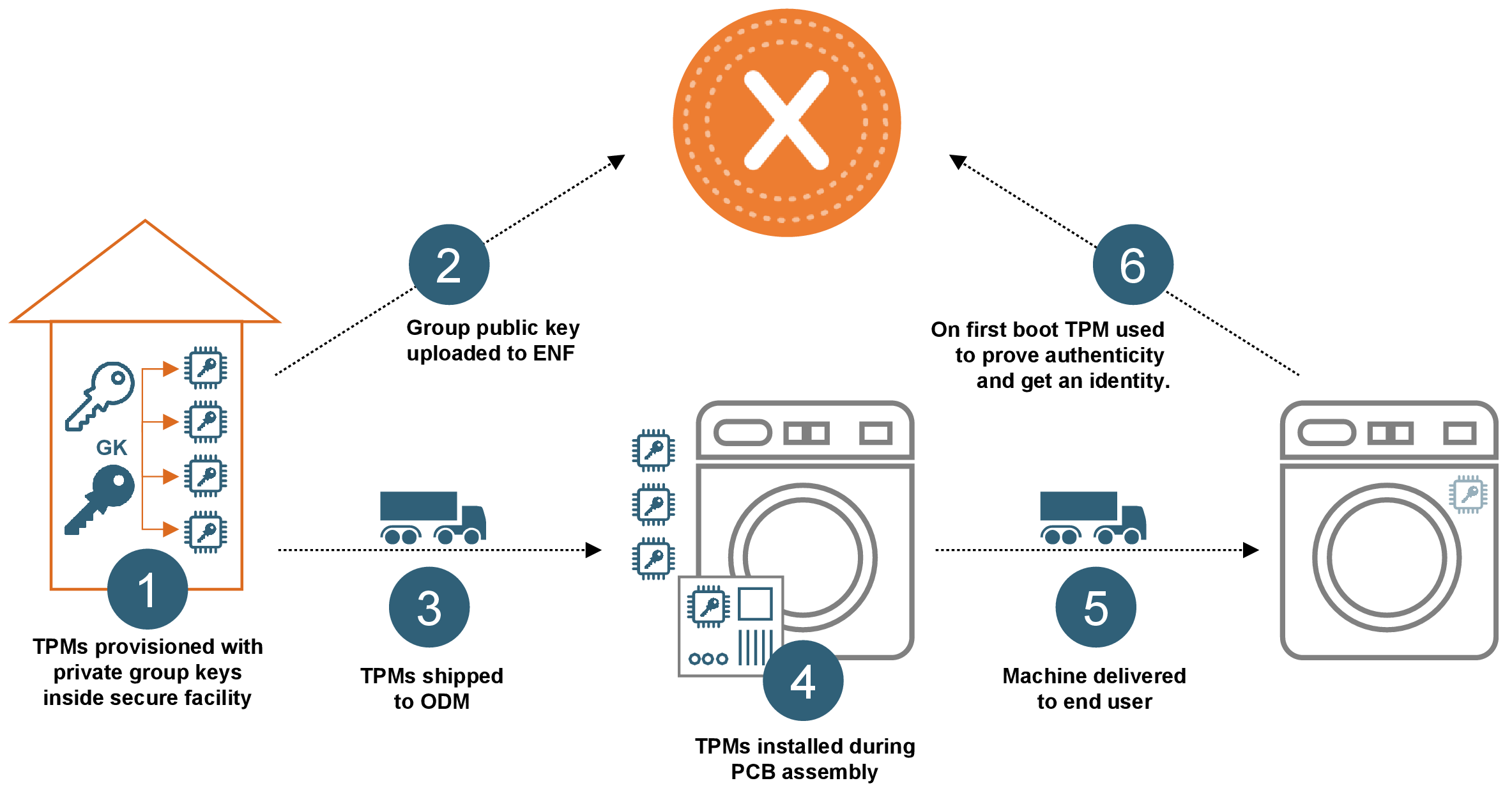
Prior to device manufacturing, secure hardware microprocessors (TPM 2.0 chips) are provisioned with unique credentials. This process can be performed in Xaptum’s secure facilities in any group size required, or handled directly by the customer:
The credentials thus generated are not yet accessible to the ENF.
The customer follows the same steps whether activating a single device or thousands of devices on a network:
This way, the customer need only scan a QR code and log in to the Xaptum management interface to enable an entire batch of devices to connect to the ENF and have identities assigned. To audit this process, the customer is also able to track the status of the individual credentials and monitor the geolocation metadata of the identity provisioning handshakes.
The provisioning handshake need only be run once. The identity assigned to the device stays assigned to it for its lifetime.
XTT is a protocol for scalable identity and credential provisioning, rooted in the trusted computing capabilities of the TPM 2.0 standard. It’s the protocol implemented to enable devices to securely access the ENF to obtain their identity.
The draft specification for this cryptographic protocol can be found here. Xaptum’s open-source implementation of this protocol is also available on GitHub.
Contact us and we’ll get back to you as soon as possible.
Contact Us