The Xaptum Edge Network Fabric is a secure, IPv6 overlay network for edge devices. An overlay network uses the physical infrastructure of one network while logically acting like a separate network. For example, in the early days, the Internet was an overlay network on top of the telephone network. Now, with VOIP, the telephone network is an overlay on top of the Internet.
The ENF isolates devices from the public Internet, while still taking advantage of the public Internet to provide global availability for devices. Devices establish a secure tunnel to the ENF over any last-mile Internet connection, much like a laptop establishing a VPN connection to an enterprise network. All traffic to the device is then routed via the ENF where malicious traffic can be monitored and blocked.
Devices can connect to the overlay via any last-mile Internet connection – even move between connections – but use a stable ENF IPv6 address for all communication. The ENF address is assigned on the first connection and, because it remains with the device forever, can be used as a stable, authenticated identifier.
The nodes on the ENF cannot directly communicate with the public Internet and vice-versa. Nodes on the public Internet are not aware of the existence of the ENF or any of the nodes. With all traffic being routed through the ENF network and firewalls, devices are isolated from the threats of the public Internet. Each customer is given a ::/48 block, which they may further partition into ::/64 subnets. Traffic between subnets is blocked by default, effectively segregating traffic within the ENF as well.
All of the communication on the ENF is encrypted using industry-standard TLS. This allows an endpoint to use an unsecured last-mile connection such as a public WiFi hotspot. To ensure that the connection between the endpoint and the ENF access point is not hijacked, the endpoint and ENF perform a two-way handshake using the ECDSA algorithm.
The Xaptum ENF is purpose-built for the edge. As a software-defined network sitting on top of the Public Internet, it secures all of a company’s connected Things anywhere in the world and protects the bidirectional exchange of data between generation at the edge and consumption at the backend.
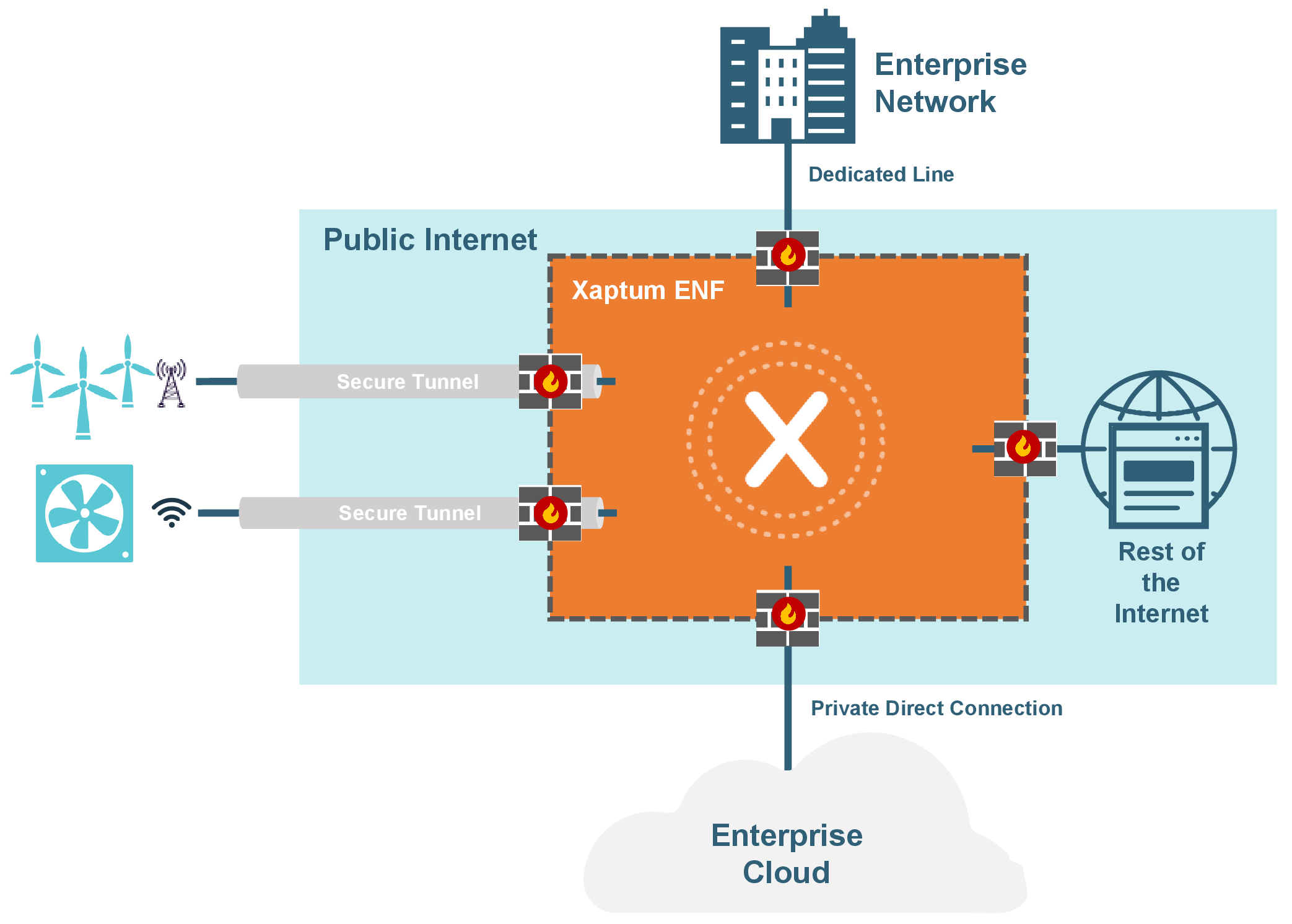
The Xaptum backbone is a distributed network of routers. This backbone has direct peering relationships to major ISPs and cloud providers to ensure fast, reliable transfer of traffic. All traffic, not just traffic from the public Internet, passes through the ENF firewall, isolating devices from malicious hosts. The firewall uses a default-deny approach. For any two nodes to communicate, firewall rules must be set up.
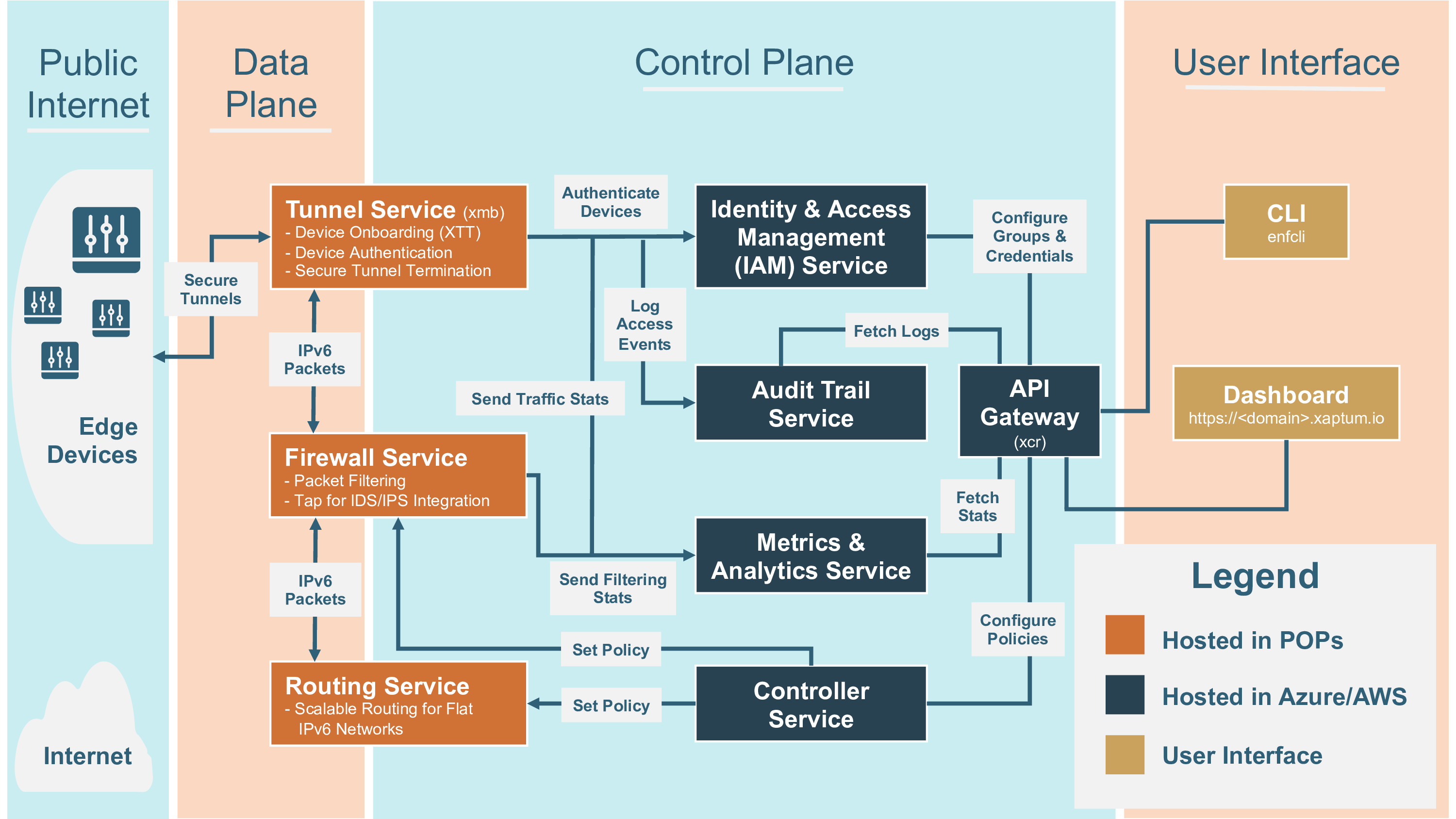
The image below illustrates the logical flow of data in the ENF. Devices establish a secure, mutually-authenticated, and encrypted tunnel over any last-mile public Internet access. Each is assigned a single IPv6 address identifying it within the customer’s network. Backend servers and cloud applications can similarly establish tunnels to receive traffic from these devices. The ENF routes traffic between the endpoints, enforces the customer-defined firewall rules, and provides visibility and control of the network.
Contact us and we’ll get back to you as soon as possible.
Contact Us