A software-defined vehicle uses hardware, firmware, and software to control and manage the operations of critical vehicle systems. The vehicle is equipped with Internet access and often with a wireless local area network (LAN). This allows the vehicle to share Internet access, and hence data, with other devices both inside as well as externally. This data enables application-based visibility and control of systems thereby delivering additional value to consumers. The connected car market is the most prominent area of software-defined vehicles and is projected to reach $225 Billion by 2025.
Despite the benefits connected cars can offer, connectivity can render the car more susceptible to cyberattacks. For example, in 2014, BMW vulnerabilities were exploited to allow unauthorized access to peripheral controls such as door locks. One year later, the industry saw a more sophisticated attack featuring zero-day exploits of relays in Jeep vehicles. In this case, the hackers were able to physically control the car while in transit. Next, a series of Tesla hacks demonstrated the flawed security of the company’s standard maintenance policies. Through various methods, hackers were able to abuse Tesla patches with unsigned updates, thereby corrupting the functionality of vehicles’ drivetrains. This progression of advanced attacks illustrates the growing problem of cybersecurity in the automotive industry.
Similar to the concept of Fly-by-Wire in aviation, Drive-by-Wire (DbW) technology in the automotive industry is the use of electrical control units (ECUs) to perform vehicle functions traditionally achieved by mechanical linkages. Subsets of connected cars, such as alternative-powered vehicles, rely more heavily on ECUs and communication over the Internet with devices and infrastructure outside of the car’s local network (e.g., backend cloud applications, traffic lights, other vehicles). This Internet connectivity can present attackers with a remote path into a vehicle’s local network and ECUs, where they can then inject malicious code to impact the physical operations of the vehicle. The most severe outcomes that hackers seek are unintended acceleration, loss of braking, and unintended steering.
Typically, an attacker executes three key steps in an attempt to cause these malicious outcomes. First, the hacker exploits a vulnerability in the communication connectivity (e.g., cellular, WiFi, Bluetooth) to gain access to a non-critical system, like the Infotainment system. Secondly, the hacker leverages the non-critical system as a bridge into critical ECUs that control vehicle operation, like Adaptive Cruise Control, Collision Prevention, and Lane Keep Assistant systems. The third and final step is to send the malicious code to the targeted ECU to disrupt the vehicle’s normal operation and cause a potentially catastrophic event.
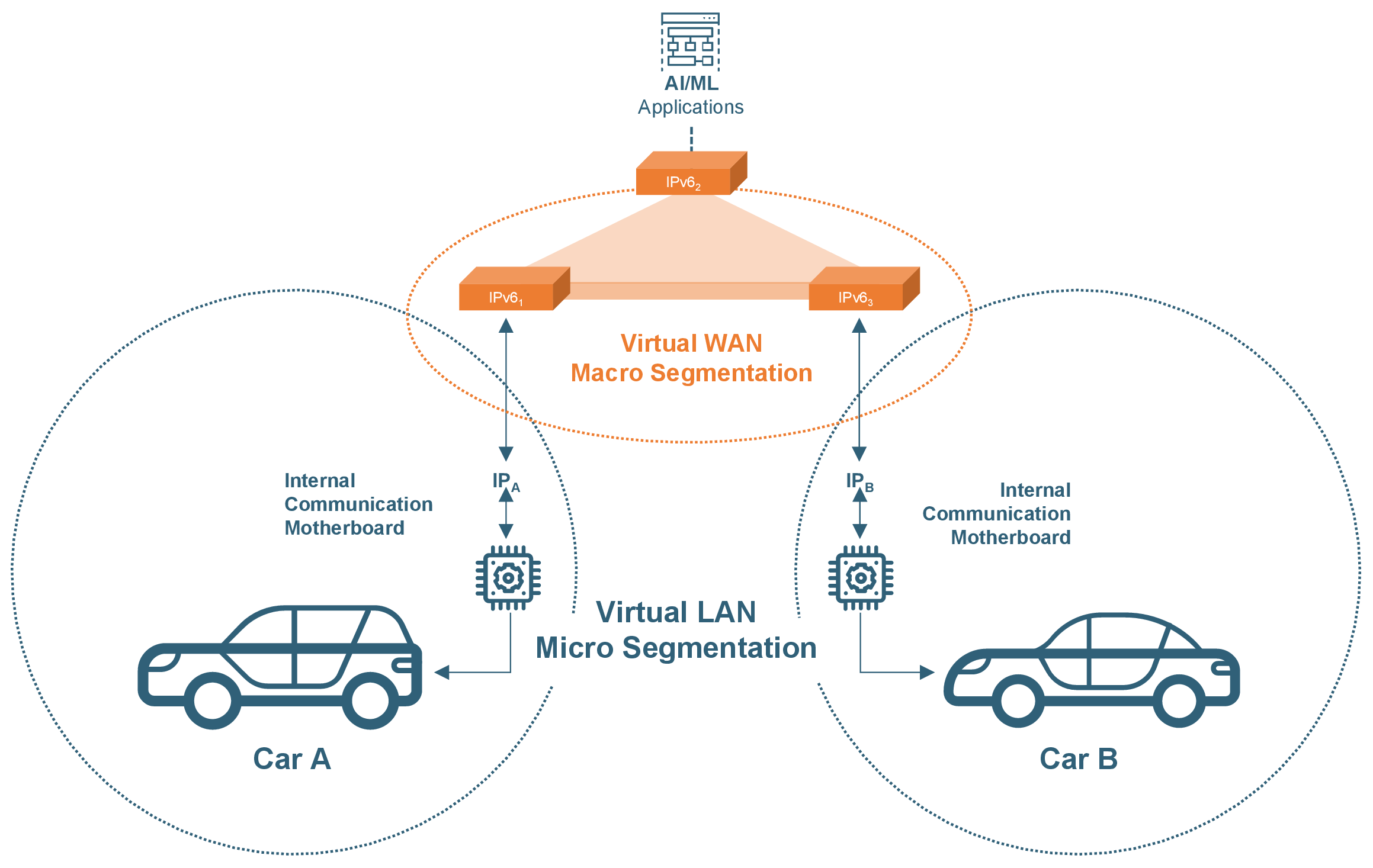
The ENF can augment and enhance the customer experience, security, reliability, and management of software-defined vehicles along three key avenues:
The ENF uses default-deny firewall rules in isolating remote endpoints to mitigate risks of lateral attacks. It functions along the “never trust, always verify” paradigm and eliminates reliance on pre-shared authentication keys used in a typical Public Key Infrastructure (PKI) approach. To learn more about how its endpoint-centric firewall enables Zero Trust Networking at scale, please refer to FAQs on the topic.
As a standards-compliant IP (layer 3) network, the ENF is agnostic to the:
Such flexibility allows customers to select the best-suited vendors and providers without any disruption. To learn more about the solution’s interoperability, please refer to the Concepts article.
Xaptum’s solution provides both software and hardware-based security against the vast amounts of threats across the public Internet. In line with ENF’s Zero Touch Provisioning , the industry-standard TPM 2.0 from Infineon is utilized for secret key generation so that ECUs can mutually authenticate themselves with other devices on the internal vehicle network and externally. To learn more about ENF’s multi-layered protection, please refer to FAQs on the topic.
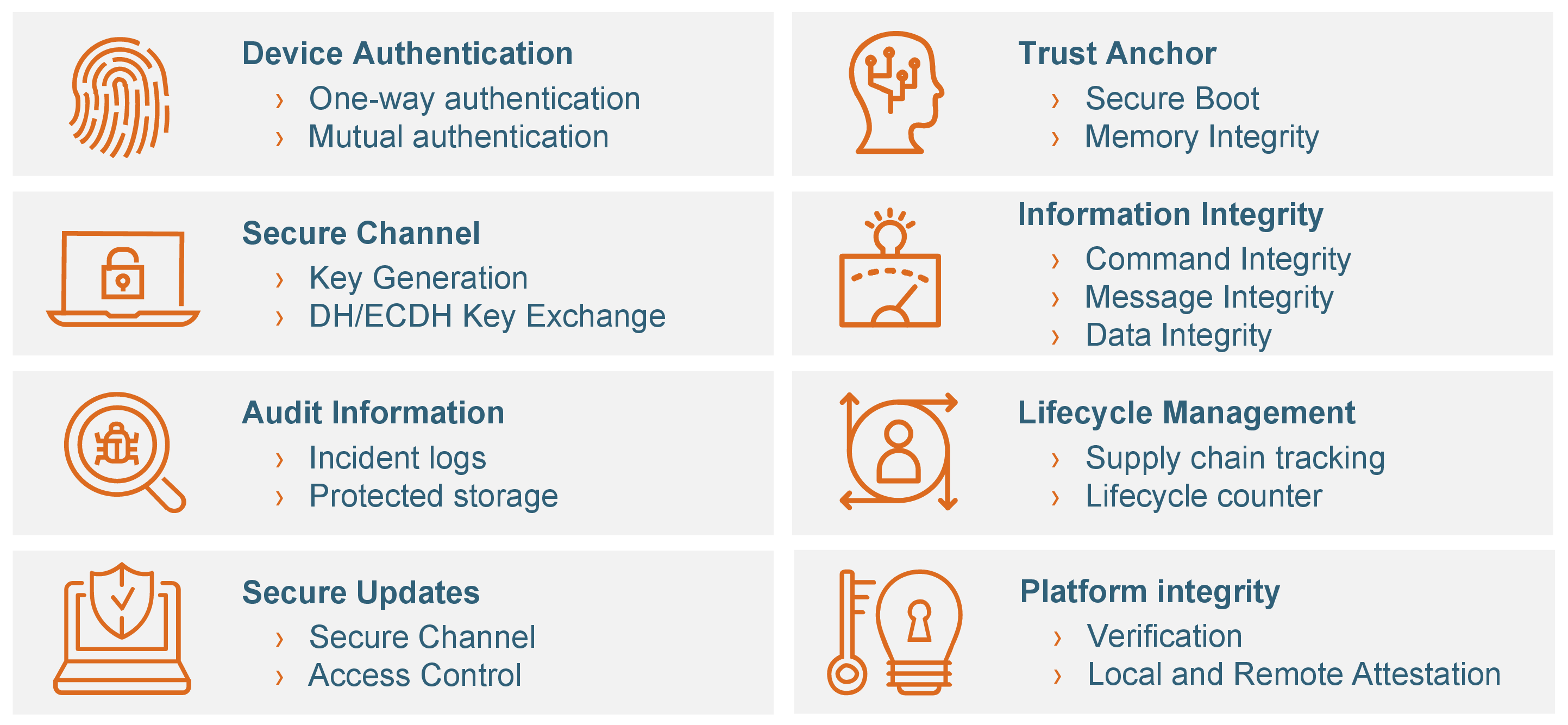
TPM Security Functions
Contact us and we’ll get back to you as soon as possible.
Contact Us