The US rail transportation sector is undergoing a massive digital transformation to improve safety and efficiency by leveraging edge computing to increase visibility, management, tracking, monitoring, and control of assets in the field. A secure move to the edge can make a tremendous impact in the following key areas within the industry:
Locomotive and Freight Wheels :
The deployment and management of network infrastructures for railroad use cases are both complex and time-intensive, creating unique security, connectivity, bandwidth, packet routing, onboarding, and scalability challenges:
Moreover, cyberattacks have the potential to disrupt production and increase costs, directly impacting business outcomes. Although cyber-insurance policies may cover some losses from cyberattacks, such coverage is unlikely to cover all losses or all types of claims that arise.
The right solution addresses these risks in providing a secure networking foundation for railroad operators, one that in turn allows them to realize the following benefits safely:
The ENF enhances the security, reliability, and management of railroad assets by providing the following key benefits:
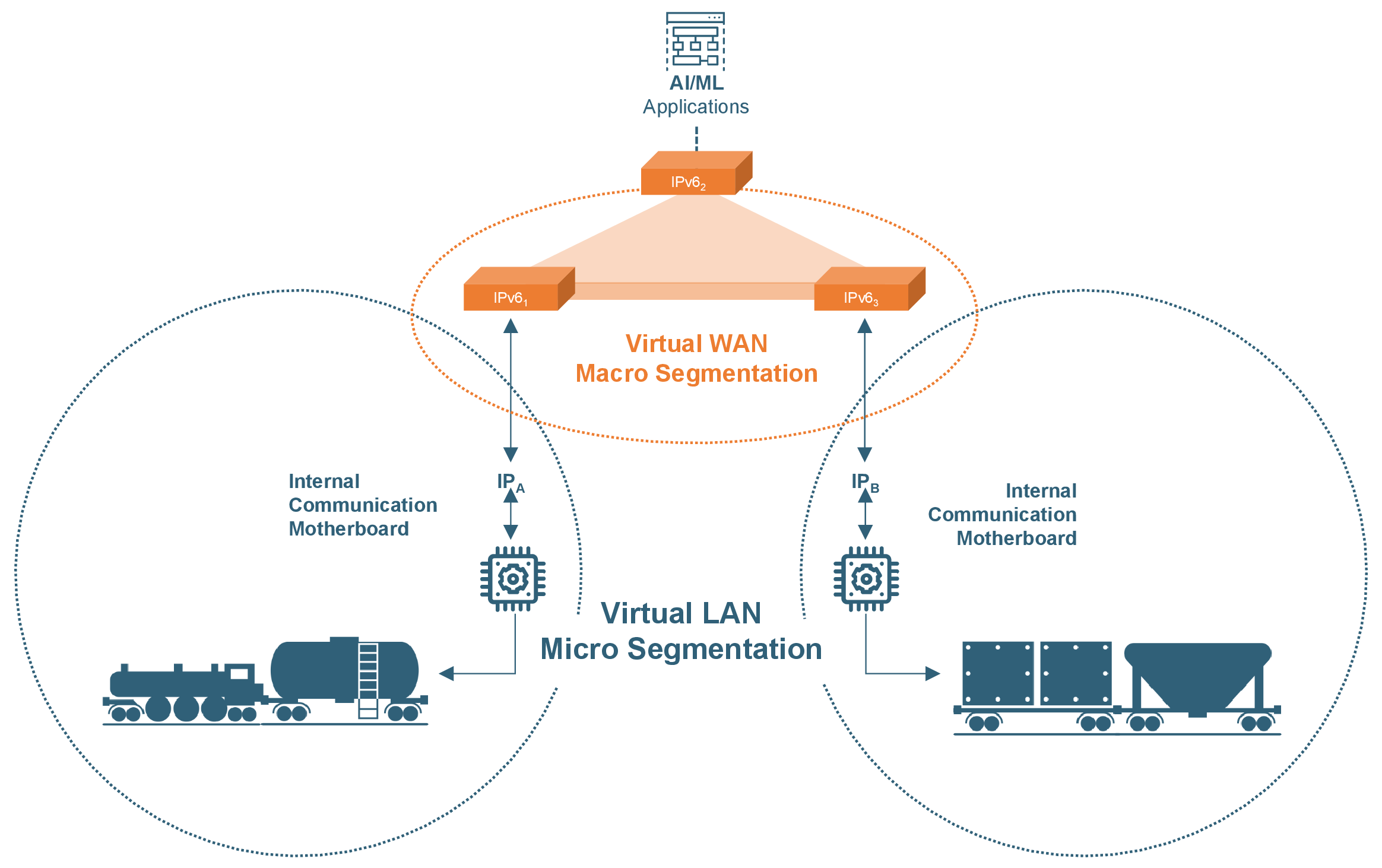
Rooted in the principle of “never trust, always verify,” ENF’s Zero Trust Networking does not assume a device is trusted just because it is connected to the network. Default-deny firewall rules are used in isolating remote endpoints to mitigate risks of lateral attacks. Furthermore, Xaptum enables microsegmentation of railroad assets based on identity, application traffic, etc., into policy-based security zones.
Xaptum enables a “Secure Access Service Edge (SASE)” that primarily acts as an Edge Proxy for security services in the cloud made available right at the edge where the devices live. This brings about the seamless delivery of required services and policy enforcements in real time, independent of device location.
The overlay network decouples the last-mile Internet access and sits between edge devices and the edge compute servers. Persistent IPv6 addresses remain unaltered with connection changes and drops along the tracks. As a standards-compliant IP (layer 3) network, ENF supports any kind of last-mile wireless access, interfaces with any cloud services, and works with any compatible hardware/gateways. To learn more about the solution’s interoperability, please refer to FAQs on the topic.
Xaptum provides both software and hardware-based security and uses the industry-standard TPM 2.0 from Infineon. Besides enabling Zero Touch Provisioning , the hardware-rooted keys and associated cryptographic functions enable a secure, hardware boot process.
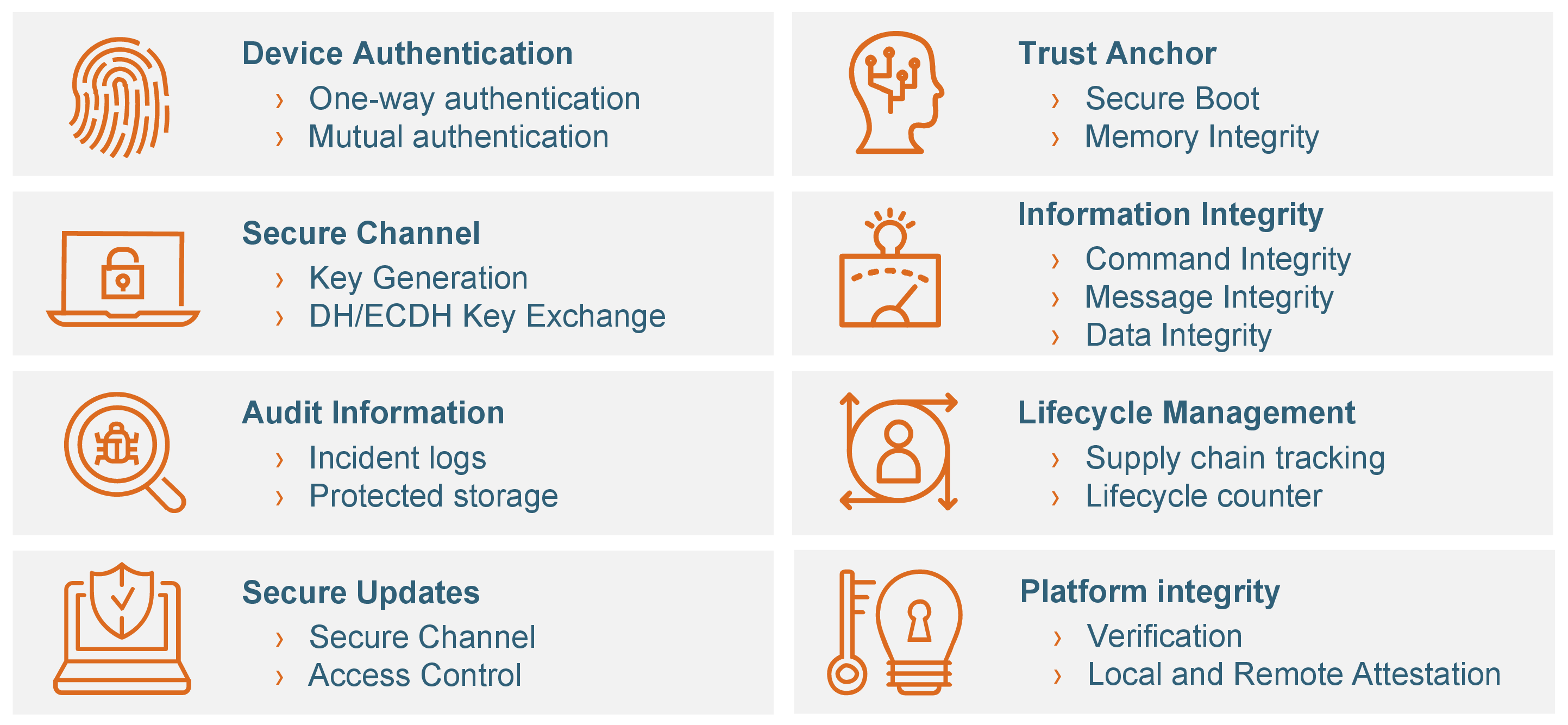
TPM Security Functions
Contact us and we’ll get back to you as soon as possible.
Contact Us