Networking dispersed or mobile assets, especially ones not originally designed with network security in mind, presents many complex security challenges. However, fields such as Industrial IoT (IIoT), military-use autonomous devices, or critical infrastructure face even greater challenges, as the assets concerned are also extremely high value. The security architectures for such use-cases must also protect against advanced threat actors (think state-sponsored groups, international criminal organizations, or well-funded competitors), who have far greater means and persistence than the typical hacker.
One such threat is longitudinal traffic sniffing: inferring sensitive intelligence based on traffic routing anomalies observed over a long period. For a simple example of this kind of threat in industrial espionage, imagine a competitor knows that a factory’s typical backend analytics platform resides in a data center in Oregon while the safety operations center is in California. By gaining access to a network exchange location (outside the control of the factory’s owner) and passively sniffing traffic, this competitor will immediately know of issues arising in the factory by simply watching for packets from the factory routed toward California.
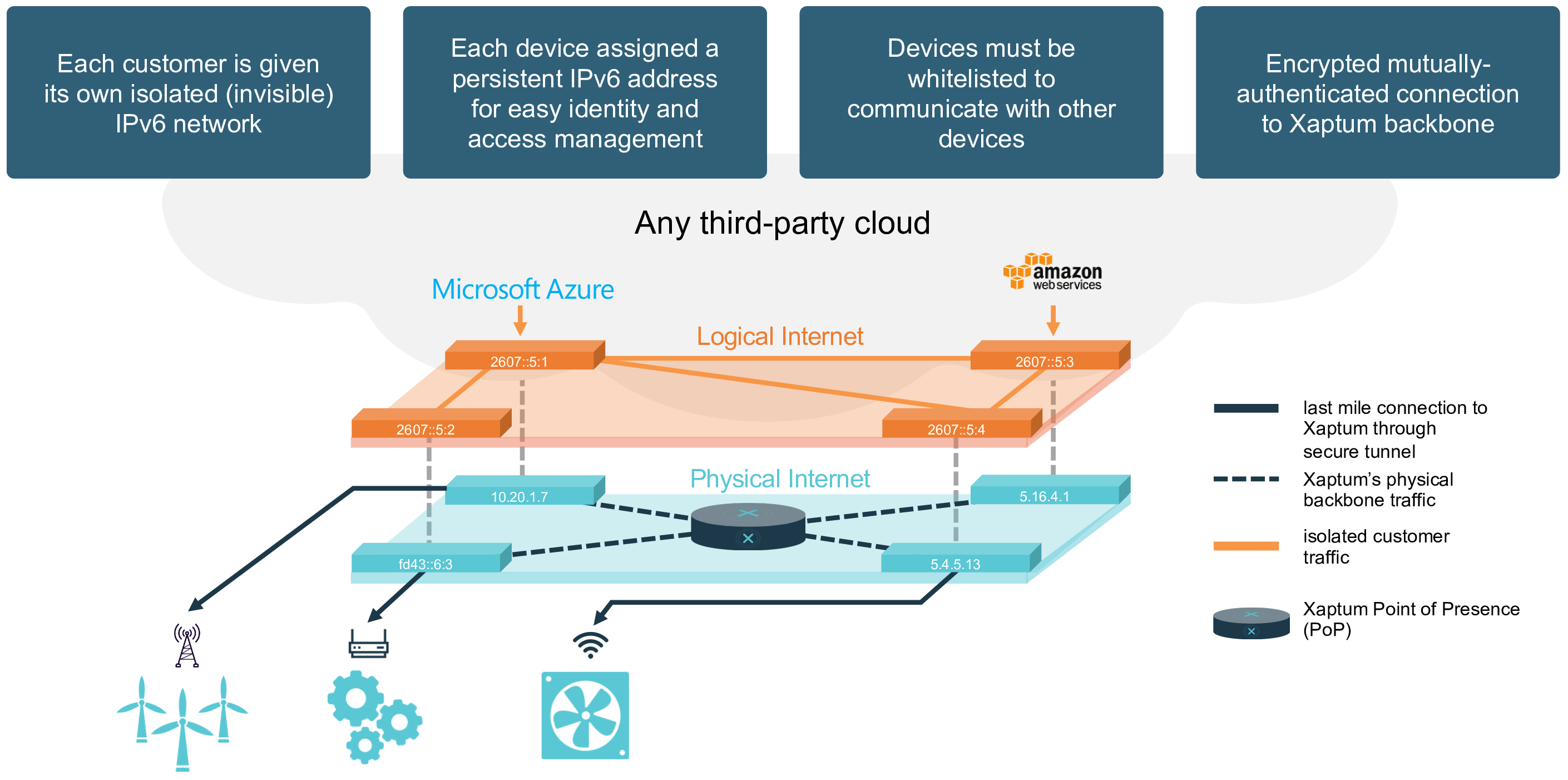
On a secure overlay network, like the Xaptum ENF, the source and destination of all packets are encrypted. Thus, this information is invisible to any sniffing.
Moreover, as routing decisions on the ENF are made within Xaptum’s backbone network, adversaries are unable to gain any knowledge of traffic routing patterns. Any traffic sniffing would reveal only that all traffic is exchanged with a Xaptum ENF server, with no revelation of its ultimate source or destination.
Contact us and we’ll get back to you as soon as possible.
Contact Us