Industrial enterprises with dispersed assets and diverse data sources are increasingly realizing that relying on conventional VPNs or point-to-point MQTT/CoAP device-to-cloud-broker connections do not scale and are not relatively secure. As Gartner recommends , today’s digital enterprises need a worldwide fabric/mesh of network and network security capabilities that can be applied when and where needed.
Whether connecting users to internal apps, extending cloud-based apps and services to the edge, etc., the underlying need generally remains the same - diverse endpoint identities requiring access to networking capabilities spread throughout the Internet at scale. Therefore, decisions on secure access and management including tracking and visibility need to be centered on the identity of the object that is at the source of the connection, e.g., user, device, service, branch office, edge computing location, etc. The enterprise data center or the cloud needn’t be the focal point of the connectivity model.
Logically assigning a permanent IP address to each device will simplify identity and access management and enable a unified view and control of dispersed assets. The simplest way to do this is to connect the device to a middle-mile network that assigns and maintains a permanent, virtual IP address to each device, unaffected by the last-mile connectivity provider.
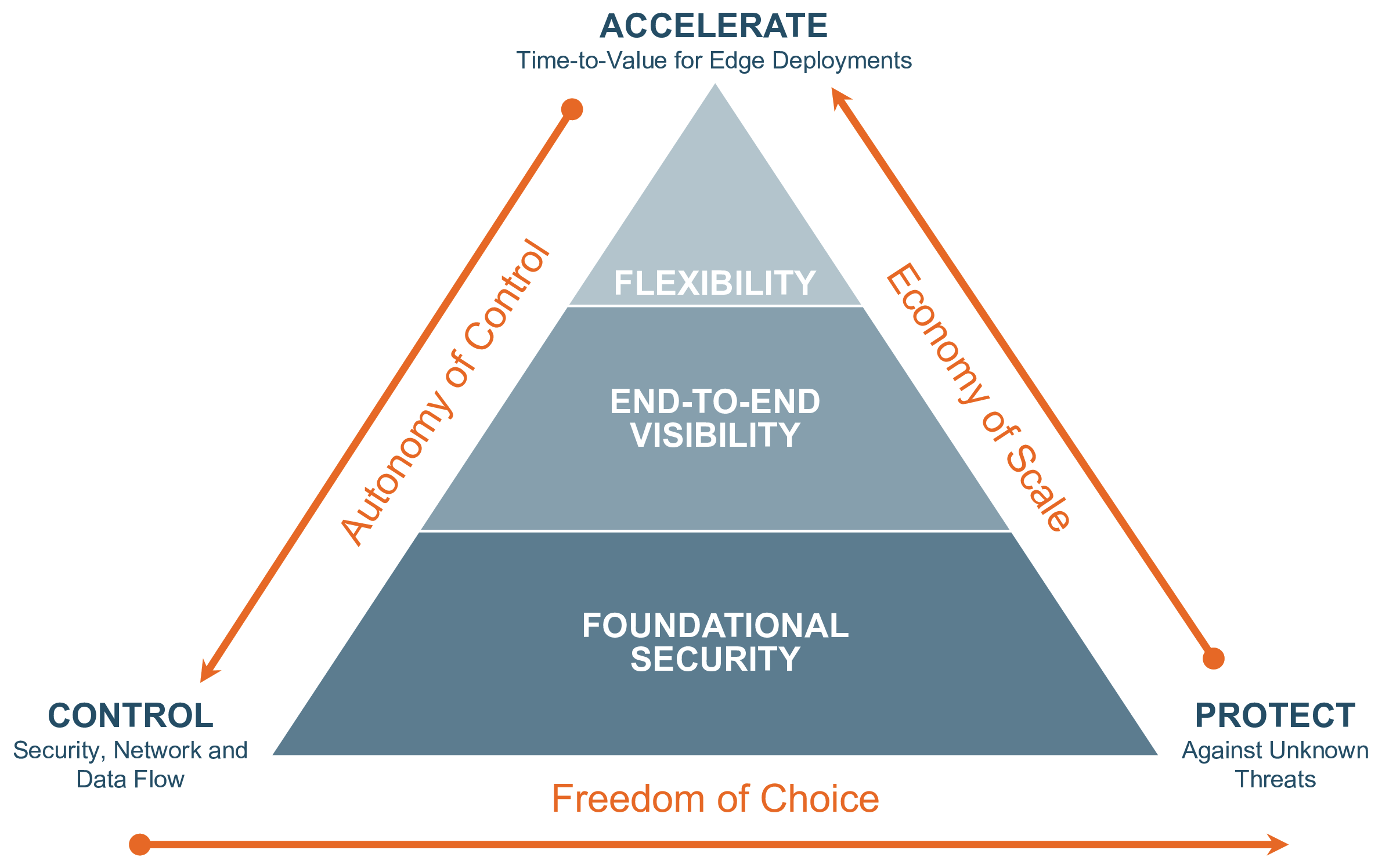
A last-mile agnostic, identity-centric, network security infrastructure supports a secure communication channel for millions of dispersed, mobile, or nomadic devices to connect and exchange data with the backend services. This dramatically simplifies the security needs for the convergence of ICS and IT infrastructure, speeding up the digital transformation process. The model also helps enterprises simplify inbound secure remote access and the connectivity needs to realize economies of scale.
Such a multi-cloud-friendly architecture aims to reduce attack surface with networking that has security and self-protection built-in, and not as afterthoughts or workarounds:
Enterprises will look to rely heavily on network slices for mission-critical IIoT applications instead of investing in building their own or relying on leased private networks for stringent security and connectivity needs. Alternatively, many enterprises may not want to invest in building internal skill sets to maintain and manage such massive services and will turn to outsourced security service vendors to assist them with their unique security requirements. For example, an enterprise might look for a globally agreed network slicing type with a stringent security requirement that works seamlessly across both the local and the visited networks providing uniform, end-to-end policy enforcement, identity and access management, tracking and visibility.
Similarly, security is a critical component of a successful 5G service delivery driven by MEC and network slicing. Instead of being forced to build out their own dedicated private networks or depend on costlier private wireless network services, enterprises must be able to rely on outsourced slicing-based security services that seamlessly scale with increasing interconnectedness and deployment of dispersed edge assets.
Contact us and we’ll get back to you as soon as possible.
Contact Us