The move to edge presents a tremendous opportunity for enterprises to digitally transform their operations. Applications including Industry 4.0, machine vision, or mobile edge computing (i.e., 5G) present a way for enterprises to gather data from their operations to automate decision making at a reduced cost. However, as enterprises deploy devices that are increasingly diverse, mobile, and/or dispersed, operational challenges around security and scale need to be overcome to make it simple for enterprises to manage them safely and seamlessly.
Edge computing has seen an increasingly large number and variety of devices with a diverse set of last-mile connectivity technologies and providers. These need to be managed together.
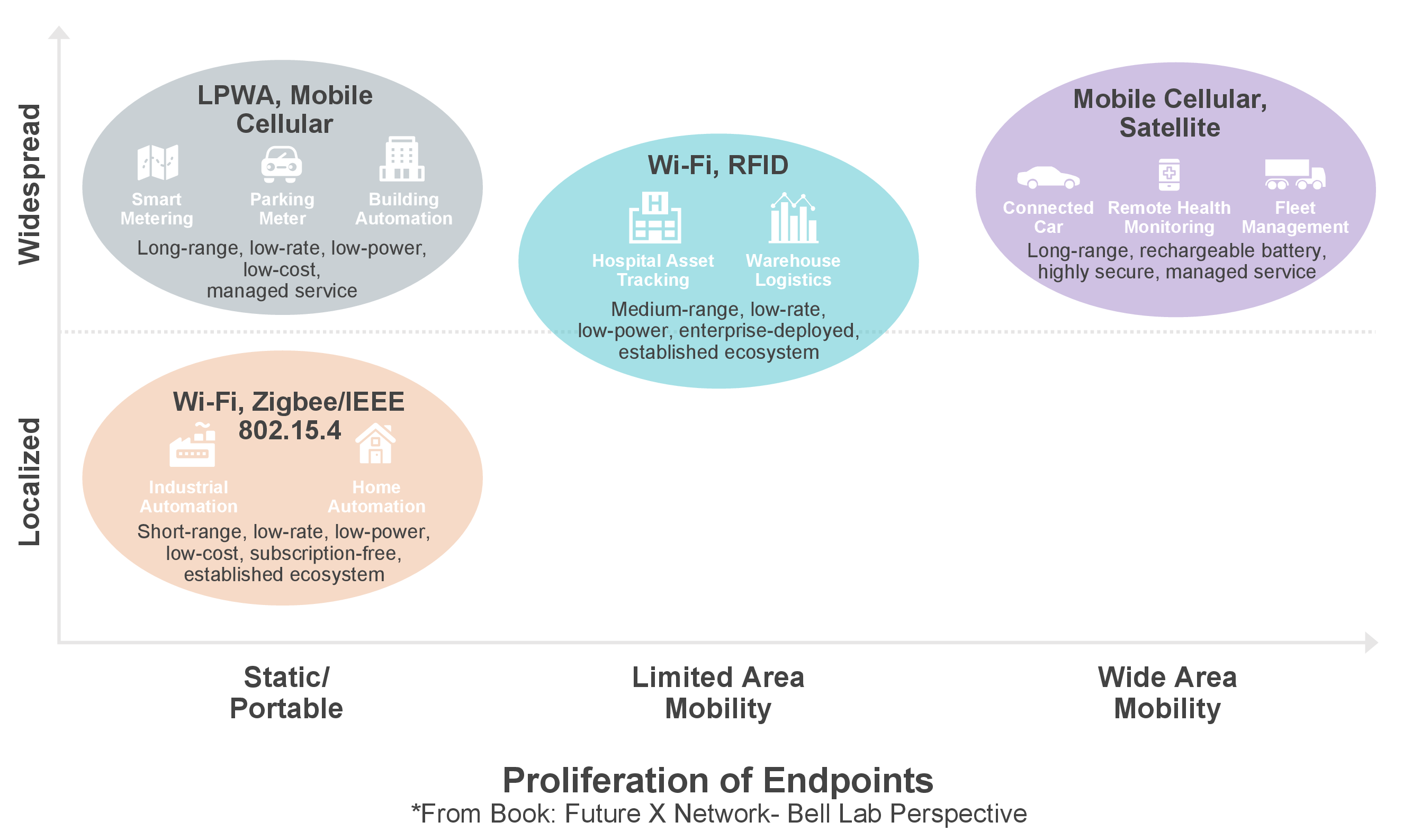
The operational approaches for management and security used in enterprise networks, where most hosts are densely contained in buildings or campuses, do not translate to the edge. Manually provisioning hundreds or thousands of devices is logistically difficult, prohibitively expensive, and error-prone. Misconfiguration is a leading cause of cybersecurity incidents. Reconfiguring and updating devices on the field is another challenge. Besides, devices located in multiple locations will likely connect over a variety of technologies and providers, such as 3G, LTE, WiFi, etc., Due to this, the devices’ IP addresses will change at arbitrary times, particularly if the device is mobile. Any configuration based on these IPs will require continuous upkeep and will often be out-of-date, making the devices difficult to manage as well as exposing them to external threats. Creating a dedicated LAN at a single site might be expensive, but is achievable. Doing the same over multiple locations or for mobile devices would be prohibitive.
A wide variety of protocols are also used for these devices to communicate with each other and to the master controller nodes. The devices must also connect to the cloud or on-premise back-office for advanced telemetry and data analytics. As a result, implementing a uniform security layer to protect these devices and the device data from unintended exposure over the public Internet is a growing need.
Industrial control systems (ICS) have always been a major part of IIoT. According to Deloitte, these systems have been connected to the IT infrastructure for years, providing remote connectivity for real-time data and remote support. The abundance of inexpensive, off-the-shelf edge computing capabilities today has made it easy to analyze this rich data for operational insights and competitive advantage. However, data collection and processing right at the edge comes with its own set of challenges and the convergence has led to expanded attack surfaces.
Device data must not be altered, i.e. its integrity needs to be preserved. Incorrect readings can easily have catastrophic results. For example, an operator may take corrective action on seeing a false low-pressure reading, which could in turn damage the equipment. Similarly, malicious actors must be denied the ability to make changes to device configuration. Purposely incorrect configuration can cause equipment damage/failure or downtime.
In larger installations, the devices in one role do not need the ability to directly communicate with those in another. For both security and management, the ability to segment the network is needed to allow fine-grain control of device interconnection. For example, the equipment on the manufacturing floor must be isolated from the rolling stock.
Devices with different connectivity providers and changing IP addresses will require constant upkeep, which is difficult and exposes them to cyberattacks. While enterprise edge networks contain legacy objects, sensors, and actuators, the traditional data center-based security approaches do not work well for dispersed objects and often lead enterprises to scale back the adoption of edge computing.
The past two decades have seen a stable demand for secure outbound remote access to enterprise IT resources (servers, applications, services, cloud, etc). With the advent of edge computing, industrial enterprises have been increasingly realizing the need for secure inbound remote access for a variety of reasons, including remote troubleshooting, run-time configuration changes, and remote monitoring. Only authorized users must be allowed access to any monitoring data.
MQTT & CoAP : Message Queuing Telemetry Transport (MQTT) and Constrained Application Protocol (CoAP) are two of the most popular publish-subscribe machine-to-machine (M2M) protocols. Both are very easy to use, adaptable and lightweight protocols suitable for effectively connecting a large array of devices over the Internet, and are specifically designed for resource-constrained, M2M use cases (e.g. low power, high latency, limited bandwidth).
However, these come with their own risks and pitfalls. A report from Trend Micro (12/2018) deeply emphasizes M2M security vulnerabilities, highlighting how attackers have been able to locate exposed servers and brokers to leak over 200 million MQTT and 19 million CoAP messages, which could then be weaponized for industrial espionage, DoS, and targeted attacks.
Traditional VPN Models : Legacy VPN models also lack the flexibility and the ability to scale to meet machine builders’ specific needs with secure inbound remote access.
Contact us and we’ll get back to you as soon as possible.
Contact Us